Guide
Everything you need to know about Information security, cybersecurity and privacy protection

JASANZ Register
Looking for help with getting certified to management system standards?
JASANZ has a Register of accredited bodies who can help.
This guide is intended to give readers in the critical minerals industries an overview of the need for the ISO/IEC TS 27 1 1 0 :20 21 standard , as well as the industry context. The risks the standards tackle and the benefits they confer are outlined below.
Internationally – approved standards help to keep information assets secure . The re are more than a dozen standards in the ISO/IEC 27000 family. Adopting them enables organi s ations to manage the security of assets such as financial information, intellectual property, employee details or information entrusted by third parties.
ISO/IEC 2 7001 , as it is widely known, is the foundation standard that outlines the requirements for an information security management system (ISMS).
It provides a model to follow when setting up and operating a management system.
This guide discusses a subsequent member of the ISO/IEC 2700 0 family that deals with cybersecurity: the ISO/IEC TS 27110:2021 standard This guide cannot display the copyrighted standard. The published standard is available for purchase from the ISO
ISO/IEC TS 27110:2021 specifies guidelines for developing a cybersecurity framework. It consists of a series of requirements consistent with other management system requirements like:
- Asset Management
- Business Continuity
- Quality, Occupational Health and Environment.
These include elements like:
- Scope and context
- Leadership, roles and responsibilities
- Risks, objectives, plans and actions
- Monitoring, support and resources
- Assessment, evaluation, review and audit.
This guide surveys changes to the standard, including:
Critical mineral businesses are becoming increasingly vulnerable to cyber-attacks because of the sheer volume of data generated and used.
Hackers and cybercrime groups pose grave threats. They can gain access to a computer network, often through third-party suppliers with weak security systems, and:
- disrupt or destroy global supply chains
- steal significant amounts of data to gain a competitive advantage and/or create financial pressure on the market
- take control of the industrial control system (ICS), mine safety systems, processing facilities, heavy machinery and/or IT environments
- compromise systems to severely disrupt mining operations
- jeopardise worker safety through attacks on underground ventilation systems, tailings dam monitoring systems or pipeline controlling systems.
Nameless Mining has discovered and proven a significant ore body of rhenium in Queensland. But the development costs are beyond their resources and they need a well-capitalised equity partner to fund and develop the mine.
While they are in discussions with a global miner, one of their FIFO workers, John, hits rock bottom at the Gold Coast casino. He’s approached by a friendly Asian gambler who notices his losses and offers to help. In return for a simple favour, all his debts can be wiped out.
On his next site visit, John unobtrusively accesses an unlocked site office late one night. In the office, he finds the network password written on a Post-It note stuck to the monitor.
He downloads highly sensitive information — all the details of the size of the deposit, purity, estimate costs of mining and a unique processing technology not yet patented. Included in the stash is confidential information about the partnership arrangement. It all fits on a thumb drive. On his next visit to the casino John hands it over to his Asian contact and clears his debts. He smiles — that was easy.
When Nameless Mining’s team next meets with their prospective partner, the tone is frosty. They’ve become aware of serious leaks of confidential information, exposing them to market rumours and potential embarrassment. Their Board is talking reputational damage. What’s worse, news has emerged of an even better rhenium ore body in Asia and the major would prefer to invest in world-class assets.
The potential partnership falls through. Potential revenue from their IP is now lost as they are unable to claim a patent. With the project now tarred by the controversy and their image as a trusted business dented, Nameless Mining is now facing an uphill battle to find a partner who can help make their mine a reality. Their future looks bleak.
The critical mining sector spend billions of dollars every year to identify potential new mining sites. Creating exploration data is very expensive and is key to any company’s growth prospects, which makes this data a lucrative target for cyber espionage.
Because the primary source of a mine’s value is its potential ore reserve, this data is often the target of cyber espionage, critically when an acquisition or merger is in the works. The aim of the cyber attackers is usually to devalue the mine and gain insider knowledge.
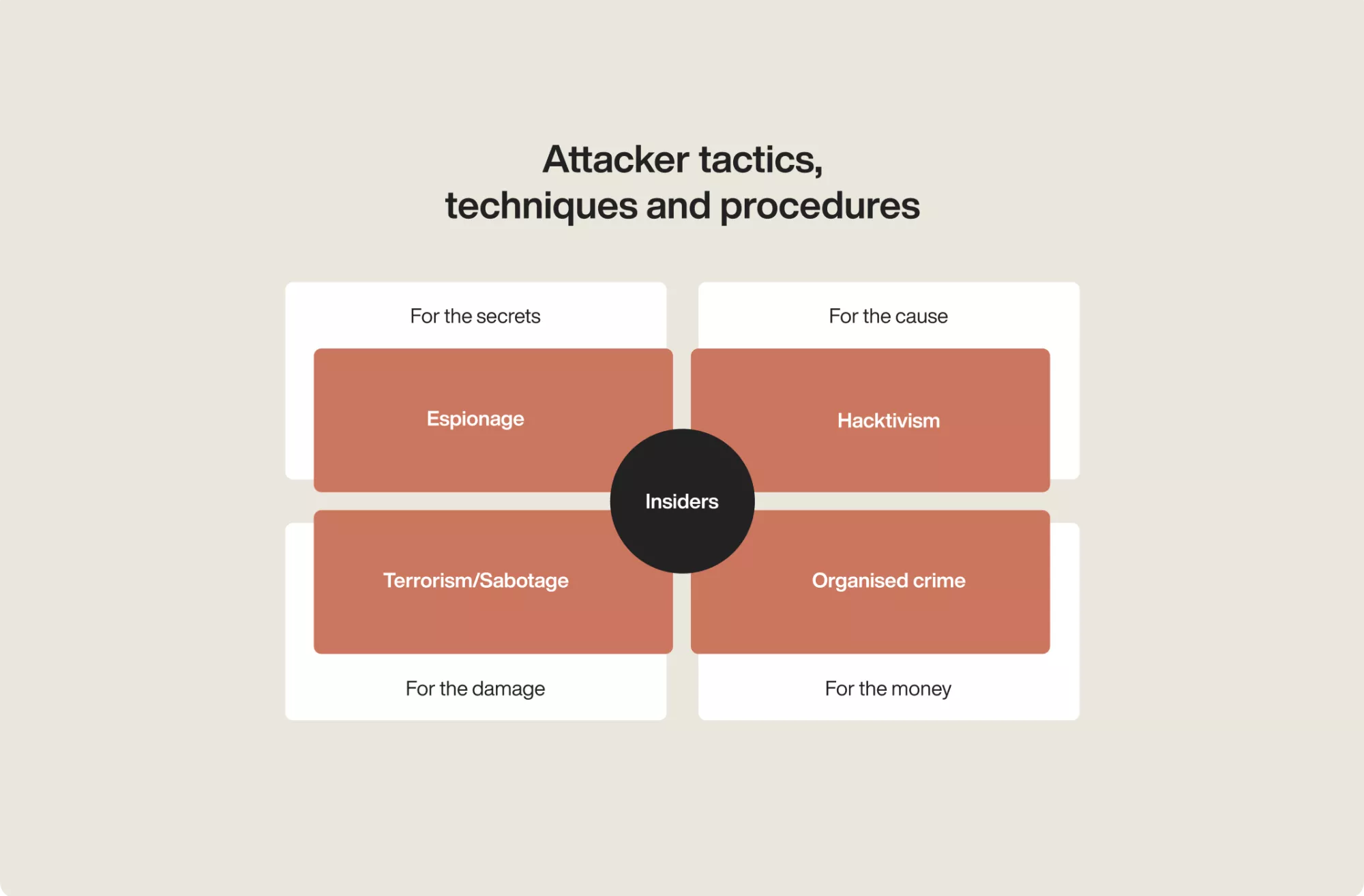
The secrets
The money
The cause
The damage
Information/cyber security
- loss of confidential data and theft of IP
- denial of service (DoS) attacks
- blackmail
- ransomware and malware
- disruption to operational systems.
New technologies like cloud computing, big data analytics, autonomous systems, and the Internet of Things (IoT) have made cyber security more complex and critical. Businesses that want to protect their assets should adopt innovative and rigorous procedures to ensure that their information assets are protected.
Information security management systems (ISMS) are designed to protect the information assets of businesses through strategic orientation, implementation and monitoring of security programs.
There are international standards for ISMS, providing a solid security framework for ensuring the confidentiality, integrity, availability, authenticity and ability to audit of critical information assets.
ISO/IEC TS 27110:2021 is designed to prepare companies for a robust and resilient cybersecurity framework for their information assets.
No. They are encouraged by the Australian Government.
Critical minerals companies that want to adopt the standards need leadership to make cyber security a business responsibility and an essential plank of corporate governance.
Adopting the standards requires considerable time, money and effort, but the benefits of adopting the standards outweigh the costs.
Information/cyber security
- creating a proactive security posture
- enhancing the management and protection of information in the organisation
- reducing vulnerabilities, threats, and risks associated with information systems
- determining roles and responsibilities regarding information security
- improving efficiency in decision-making by articulating business objectives and providing more focused management information
- enhancing availability, confidentiality and integrity of information
- creating plans for business continuity and disaster recovery
- improving confidence and competitiveness, and providing a framework for risk management at the national and international levels
- maintaining the organisation’s reputation and placing it among industry leaders
- building confidence for customers, partners, and stakeholders that the organisation is committed to protecting data
- increasing the company’s revenue, profitability, and savings of industry by using protective controls effectively
- performing optimally in the face of disparate risks and multiple uncertainties.
No.
Due to the rapidly changing nature of information technology and cyber security, there are three international standards that cover this area.
Information/cyber security
- ISO/IEC 27001:2013 — Information technology — Security techniques — Information security management systems — Requirements
- ISO/IEC 27002:2022 — Information security, cybersecurity and privacy protection — Information security controls
- ISO/IEC TS 27110:2021 — Information technology, cybersecurity and privacy protection — Cybersecurity framework development guidelines
In practice, while the ISO/IEC 27001:2013 standard has the most thorough coverage of information security topics, it has limits and is often augmented by other technical standards that provide additional controls. These are the related standards:
- NIST (National Institute of Standards and Technology) Cybersecurity Framework (CSF)
- NIST Special Publication (SP) 800-53
- The Centre of Internet Security (CIS) Critical Controls
- The Cloud Security Alliance (CSA) Cloud Control Matrix (CCM)
- Consensus Assessment Initiative Questionnaire (CAIQ).
It makes sense to augment controls in ISO/IEC 27001:2013 Annex A with controls from more technical standards in the case of sector-specific requirements.
For example:
- Financial services — more controls to prevent fraud such as identity verification and anti-money laundering
- Energy sector — controls that relate to Operational Technology
- NIST CSF — critical infrastructure and cyber-orientated organisations
- NIST SP 800-53 — critical infrastructure and government departments and organisations doing business with them
- CSA CCM/CAIQ — cloud-orientated service provider
- CIS Critical Controls — internet-enabled organisations, particularly those managing platform infrastructure (e.g., operating systems) that requires hardening.
ISO/IEC 27001:2013 offers the strongest framework for tailoring controls based on effective risk and security program management. It focuses on an information security management system (ISMS).
The technical standards cover areas not dealt with in such detail, such as cybersecurity, critical infrastructure and cloud services. Integrating these additional controls is encouraged under the ISO/IEC 27001:2013 framework. Organisations should assess their situation and information security needs against the standards to select the appropriate standards for their operations.
ISO/IEC TS 27110 was introduced by ISO/IEC in 2021 and expands the focus of the ISO 27000 series from a traditional information security orientation to include cybersecurity.
The technical specification does this by detailing five cybersecurity concepts:
- Identify
- Detect
- Protect
- Respond
- Recover
This terminology was first popularised by NIST when it published the first version of the NIST CSF in 2014
The Identify, Detect, Protect, Respond and Recover cybersecurity language is very appealing to cybersecurity practitioners because it relates to the layers of activities required to stop or otherwise limit the damage caused by cyber adversaries.
- Identify – The Identify concept develops the organisational understanding required to manage cybersecurity risks. ISO/IEC 27002 refers to this as an ecosystem.
- Protect – The Protect concept develops appropriate safeguards to ensure delivery of critical services. ISO/IEC 27002 refers to this as protecting the organisation’s cyber persona.
- Detect – The Detect concept sees that the organisation develops and implements appropriate activities to identify the occurrence of a cybersecurity event.
- Respond – The Respond concept relates to developing and implementing appropriate activities to take action regarding a detected cybersecurity incident.
- Recover – Finally, the Recover concept involves developing and implementing appropriate activities to maintain plans for resilience and to restore capabilities or services impaired by a cybersecurity incident.
The Identify, Detect, Protect, Respond and Recover cybersecurity language is very appealing to cybersecurity practitioners because it relates to the layers of activities required to stop or otherwise limit the damage caused by cyber adversaries.
- Identify – The Identify concept develops the organisational understanding required to manage cybersecurity risks. ISO/IEC 27002 refers to this as an ecosystem.
- Protect – The Protect concept develops appropriate safeguards to ensure delivery of critical services. ISO/IEC 27002 refers to this as protecting the organisation’s cyber persona.
- Detect – The Detect concept sees that the organisation develops and implements appropriate activities to identify the occurrence of a cybersecurity event.
- Respond – The Respond concept relates to developing and implementing appropriate activities to take action regarding a detected cybersecurity incident.
- Recover – Finally, the Recover concept involves developing and implementing appropriate activities to maintain plans for resilience and to restore capabilities or services impaired by a cybersecurity incident.
When applying these concepts in response to risk management needs. These are the specific business drivers relevant to the mining and minerals sector:
- Maintain safety of facilities and protection of life (and contributes to continuity of operations)
- Maintain continuity of operations (to minimise disruption and maximise wealth generation)
- Minimise losses associated with successful cyberattacks including regulatory intervention
- Protect intellectual property (to maximise competitive advantage).
A cybersecurity framework creator needs to identify which categories, subcategories and activities of the various standards are relevant in their circumstances.
They should follow the standards mappings provided below to extract and present an easily accessible framework.
Cybersecurity framework creators should be aware of the differences (i.e., additions and subtractions) between ISO/IEC 27110 Annexures and the NIST CSF.
The following table summarises the mapping of ISO/IEC TS 27110 Categories to the NIST CSF functions.
|
ISO/IEC 27110 Category |
Cybersecurity Concept |
NIST Function |
NIST Category Identifier |
NIST Category |
|---|---|---|---|---|
|
Business environment |
Identify |
Identify |
ID.BE |
Business Environment |
|
Context |
Identify |
Identify |
ID.BE |
Business Environment |
|
Asset management |
Identify |
Identify |
ID.AM |
Asset management |
|
Risk assessment |
Identify |
Identify |
ID.RA |
Risk assessment |
|
Governance |
Identify |
Identify |
ID.GV |
Governance |
|
Risk management strategy |
Identify |
Identify |
ID.RM |
Risk management strategy |
|
Supply Chain |
Identify |
Identify |
ID.SC |
Supply Chain Risk Management |
|
Prevention |
Protect |
Protect |
PR.PT |
Protective Technology |
|
Assessment |
Protect |
– |
– |
– |
|
Lifecycle security |
Protect |
Protect |
PR.IP |
Information Protection Processes and Procedures |
|
Anomalies and events |
Detect |
Detect |
DE.AE |
Anomalies and Events |
|
Security monitoring capabilities |
Detect |
Detect |
DE.CM |
Security Continuous Monitoring |
|
Detection activity |
Detect |
Detect |
DE.DP |
Detection Process |
|
Information protection |
Detect |
Protect |
PR.IP |
Information Protection Processes and Procedures |
|
Response plans |
Respond |
Respond |
RS.RP |
Response Planning |
|
Response execution |
Respond |
Protect |
PR.IP |
Information Protection |
|
Reporting |
Respond |
– |
– |
– |
|
Communication with competent authorities |
Respond |
Respond |
RS.RO |
Communications |
|
Recovery planning |
Recover |
Recover |
RC.RP |
Recovery Planning |
|
Recovery Training |
Recover |
– |
– |
– |
|
Recovery Execution |
Recover |
Protect |
PR.IP |
Information Protection |